우분투 24.04에서 3대의 노드를 사용하여 Consul 백엔드 기반의 Vault HA 클러스터를 구성하는 방법
우분투 24.04 환경에서 3대의 노드를 사용하여 Consul을 Storage Backend로 사용하는 Vault HA 클러스터를 구성하는 방법입니다. Consul은 데이터 저장소 및 HA 조정 역할을 수행하고 Vault는 Active/Standby 구조로 동작합니다.
테스트 환경
| 호스트 이름 | 아이피 주소 | 운영체제 정보 | 비고 |
| node141 | 192.168.0.141 | 우분투 24.04 | |
| node142 | 192.168.0.142 | 우분투 24.04 | |
| node143 | 192.168.0.143 | 우분투 24.04 |
아키텍처
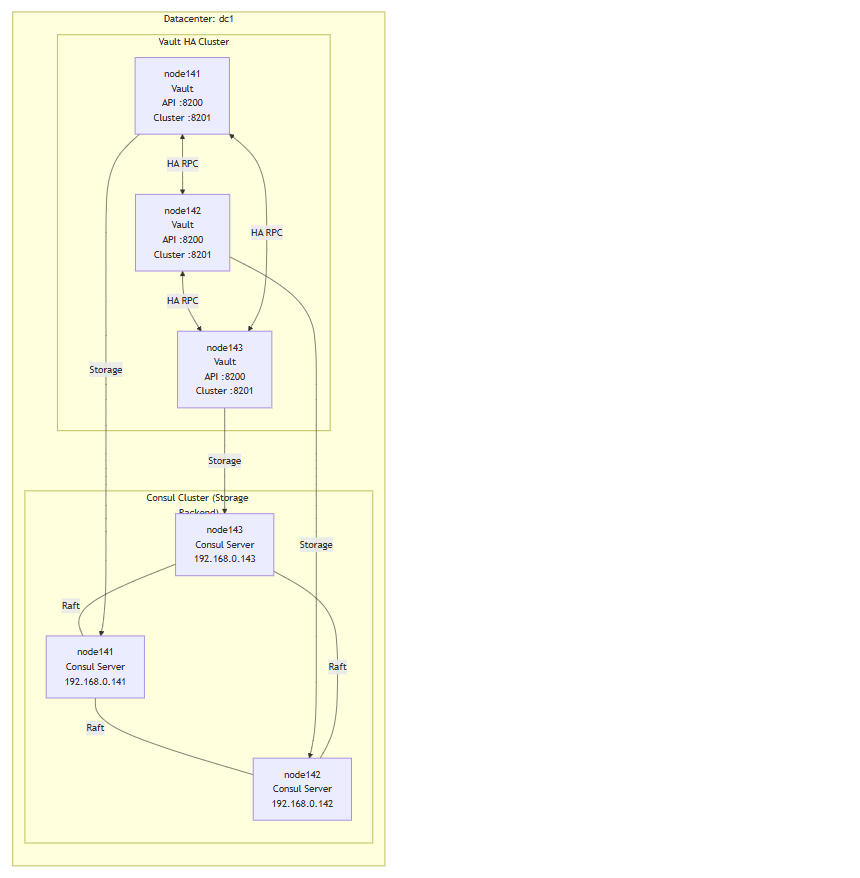
1. 사전 준비(모든 노드)
시스템 업데이트
sudo apt update필수 패키지 설치
sudo apt install -y wget curl unzip jq/etc/hosts 설정
sudo tee -a /etc/hosts << EOF
192.168.0.141 node141
192.168.0.142 node142
192.168.0.143 node143
EOF2. Consul 클러스터 구성(Storage Layer)
Consul 설치 (모든 노드)
# Consul 다운로드
CONSUL_VERSION="1.22.3"
wget https://releases.hashicorp.com/consul/${CONSUL_VERSION}/consul_${CONSUL_VERSION}_linux_amd64.zip
#wget https://releases.hashicorp.com/consul/1.22.3/consul_1.22.3_linux_amd64.zip
# 압축 해제 및 설치
unzip consul_${CONSUL_VERSION}_linux_amd64.zip
sudo mv consul /usr/local/bin/
sudo chmod +x /usr/local/bin/consul
sudo consul --versionConsul 사용자 및 디렉토리 생성
sudo useradd --system --home /etc/consul.d --shell /bin/false consul
sudo mkdir -p /opt/consul /etc/consul.d /var/log/consul
sudo chown -R consul:consul /opt/consul /etc/consul.d /var/log/consulConsul Gossip 암호화 키 생성(node141)
암호화 키 생성
consul keygenKL0TfkyzjCKs04Ft3ppEJfEOEYJcdBr6IcL55FZFrOk=- 생성된 키를 복사해두고 모든 노드의 설정에 사용합니다.
Consul 설정 파일 생성(모든 노드)
/etc/consul.d/consul.hcl 파일
sudo tee /etc/consul.d/consul.hcl << 'EOF'
datacenter = "dc1"
node_name = "node141"
encrypt = "YOUR_ENCRYPTION_KEY_HERE"
server = true
bootstrap_expect = 3
bind_addr = "192.168.0.141"
client_addr = "0.0.0.0"
data_dir = "/opt/consul"
log_level = "INFO"
log_file = "/var/log/consul/consul.log"
retry_join = [
"192.168.0.141",
"192.168.0.142",
"192.168.0.143"
]
ui_config {
enabled = true
}
performance {
raft_multiplier = 1
}
EOFnode141
sed -i 's/^encrypt\s*=\s*".*"/encrypt = "KL0TfkyzjCKs04Ft3ppEJfEOEYJcdBr6IcL55FZFrOk="/' /etc/consul.d/consul.hclnode142
sed -i \
-e 's/^node_name\s*=\s*"node141"/node_name = "node142"/' \
-e 's/^encrypt\s*=\s*".*"/encrypt = "KL0TfkyzjCKs04Ft3ppEJfEOEYJcdBr6IcL55FZFrOk="/' \
-e 's/^bind_addr\s*=\s*"192\.168\.0\.141"/bind_addr = "192.168.0.142"/' \
/etc/consul.d/consul.hclnode143
sed -i \
-e 's/^node_name\s*=\s*"node141"/node_name = "node143"/' \
-e 's/^encrypt\s*=\s*".*"/encrypt = "KL0TfkyzjCKs04Ft3ppEJfEOEYJcdBr6IcL55FZFrOk="/' \
-e 's/^bind_addr\s*=\s*"192\.168\.0\.141"/bind_addr = "192.168.0.143"/' \
/etc/consul.d/consul.hcl파일 권한 설정(모든 노드)
sudo chown -R consul:consul /etc/consul.d
sudo chmod 640 /etc/consul.d/consul.hclConsul 설정 검증(유효성 검사)
sudo consul validate /etc/consul.d/서비스 등록(모든 노드)
systemd 서비스 생성
sudo tee /etc/systemd/system/consul.service << 'EOF'
[Unit]
Description=Consul
Documentation=https://www.consul.io/
Requires=network-online.target
After=network-online.target
[Service]
User=consul
Group=consul
ExecStart=/usr/local/bin/consul agent -config-dir=/etc/consul.d/
ExecReload=/bin/kill --signal HUP $MAINPID
KillMode=process
KillSignal=SIGTERM
Restart=on-failure
LimitNOFILE=65536
[Install]
WantedBy=multi-user.target
EOFConsul 서비스 시작 및 활성화
sudo systemctl daemon-reload
sudo systemctl --now enable consul상태 확인
Consul 서비스 상태
sudo systemctl status consulConsul 클러스터 상태 확인
consul membersNode Address Status Type Build Protocol DC Partition Segment
node141 192.168.0.141:8301 alive server 1.22.3 2 dc1 default <all>
node142 192.168.0.142:8301 alive server 1.22.3 2 dc1 default <all>
node143 192.168.0.143:8301 alive server 1.22.3 2 dc1 default <all>consul operator raft list-peersNode ID Address State Voter RaftProtocol Commit Index Trails Leader By
node141 ade7a77e-1782-e1ee-ff3d-8b427f64c765 192.168.0.141:8300 leader true 3 1256 -
node142 914d1027-ae17-d57f-ec40-ac209add7b39 192.168.0.142:8300 follower true 3 1256 0 commits
node143 ea1ca0bb-6ad8-f2f4-109a-7d0d80ad1a71 192.168.0.143:8300 follower true 3 1256 0 commits3. Vault HA 클러스터 구성(Application Layer)
Vault 설치(모든 노드)
# Vault 다운로드
VAULT_VERSION="1.21.3"
wget https://releases.hashicorp.com/vault/${VAULT_VERSION}/vault_${VAULT_VERSION}_linux_amd64.zip
#wget https://releases.hashicorp.com/vault/1.21.3/vault_1.21.3_linux_amd64.zip
# 압축 해제 및 설치
unzip vault_${VAULT_VERSION}_linux_amd64.zip
sudo mv vault /usr/local/bin/
sudo chmod +x /usr/local/bin/vault
sudo vault versionVault 사용자 및 디렉토리 생성
sudo useradd --system --home /etc/vault.d --shell /bin/false vault
sudo mkdir -p /opt/vault /etc/vault.d /var/log/vault
sudo chown -R vault:vault /opt/vault /etc/vault.d /var/log/vault
sudo chmod 750 /var/log/vaultVault 서버에 TLS 설정(모든 노드)
자체 서명 인증서 생성(테스트용)
sudo mkdir -p /opt/vault/tlsOpenSSL 설정 파일 생성
- node141
sudo tee /opt/vault/tls/openssl.cnf << 'EOF'
[req]
default_bits = 4096
distinguished_name = req_distinguished_name
req_extensions = v3_req
prompt = no
[req_distinguished_name]
C = KR
ST = Incheon
L = Incheon
O = Vault
CN = vault.local
[v3_req]
keyUsage = keyEncipherment, dataEncipherment
extendedKeyUsage = serverAuth
subjectAltName = @alt_names
[alt_names]
DNS.1 = vault.local
DNS.2 = node141
DNS.3 = localhost
IP.1 = 192.168.0.141
IP.2 = 127.0.0.1
EOF- node142
---
sudo tee /opt/vault/tls/openssl.cnf << 'EOF'
[req]
default_bits = 4096
distinguished_name = req_distinguished_name
req_extensions = v3_req
prompt = no
[req_distinguished_name]
C = KR
ST = Incheon
L = Incheon
O = Vault
CN = vault.local
[v3_req]
keyUsage = keyEncipherment, dataEncipherment
extendedKeyUsage = serverAuth
subjectAltName = @alt_names
[alt_names]
DNS.1 = vault.local
DNS.2 = node142
DNS.3 = localhost
IP.1 = 192.168.0.142
IP.2 = 127.0.0.1
EOF---
- node143
---
sudo tee /opt/vault/tls/openssl.cnf << 'EOF'
[req]
default_bits = 4096
distinguished_name = req_distinguished_name
req_extensions = v3_req
prompt = no
[req_distinguished_name]
C = KR
ST = Incheon
L = Incheon
O = Vault
CN = vault.local
[v3_req]
keyUsage = keyEncipherment, dataEncipherment
extendedKeyUsage = serverAuth
subjectAltName = @alt_names
[alt_names]
DNS.1 = vault.local
DNS.2 = node143
DNS.3 = localhost
IP.1 = 192.168.0.143
IP.2 = 127.0.0.1
EOF---
인증서 생성
sudo openssl req -x509 -nodes -newkey rsa:4096 \
-keyout /opt/vault/tls/vault-key.pem \
-out /opt/vault/tls/vault-cert.pem \
-days 365 \
-config /opt/vault/tls/openssl.cnf \
-extensions v3_req권한 설정
sudo chown -R vault:vault /opt/vault/tls
sudo chmod 600 /opt/vault/tls/vault-key.pem
sudo chmod 644 /opt/vault/tls/vault-cert.pemVault 설정 파일 생성
/etc/vault.d/vault.hcl(node141 기준)
sudo tee /etc/vault.d/vault.hcl << 'EOF'
ui = true
storage "consul" {
address = "127.0.0.1:8500"
path = "vault/"
}
listener "tcp" {
address = "192.168.0.141:8200"
tls_cert_file = "/opt/vault/tls/vault-cert.pem"
tls_key_file = "/opt/vault/tls/vault-key.pem"
}
log_level = "info"
log_file = "/var/log/vault/"
api_addr = "https://192.168.0.141:8200"
cluster_addr = "https://192.168.0.141:8201"
EOFnode142
sed -i 's/192\.168\.0\.141/192.168.0.142/g' /etc/vault.d/vault.hclnode143
sed -i 's/192\.168\.0\.141/192.168.0.143/g' /etc/vault.d/vault.hcl파일 권한 설정(모든 노드)
sudo chown -R vault:vault /etc/vault.d
sudo chmod 640 /etc/vault.d/vault.hclVault 설정 검증(유효성 검사)
vault server -config=/etc/vault.d/vault.hcl==> Vault server configuration:
Administrative Namespace:
Api Address: http://192.168.0.143:8200
Cgo: disabled
Cluster Address: https://192.168.0.143:8201
Environment Variables: HISTSIZE, HISTTIMEFORMAT, HOME, LANG, LESSCLOSE, LESSOPEN, LOGNAME, LS_COLORS, MAIL, OLDPWD, PATH, PS1, PWD, SHELL, SHLVL, TERM, TIMEOUT, USER, XDG_DATA_DIRS, _
Go Version: go1.25.6
Listener 1: tcp (addr: "192.168.0.143:8200", cluster address: "192.168.0.143:8201", disable_request_limiter: "false", max_json_array_element_count: "10000", max_json_depth: "300", max_json_object_entry_count: "10000", max_json_string_value_length: "1048576", max_request_duration: "1m30s", max_request_size: "33554432", tls: "disabled")
Log Level: info
Mlock: supported: true, enabled: true
Recovery Mode: false
Storage: consul (HA available)
Version: Vault v1.21.3, built 2026-02-03T14:56:30Z
Version Sha: f4f0f4eb7f467bbc99ec89121e1d1ad9c3d78558
==> Vault server started! Log data will stream in below:
2026-02-10T12:03:46.768+0900 [INFO] proxy environment: http_proxy="" https_proxy="" no_proxy=""
2026-02-10T12:03:46.778+0900 [INFO] incrementing seal generation: generation=1
2026-02-10T12:03:46.963+0900 [INFO] core: Initializing version history cache for core
2026-02-10T12:03:46.963+0900 [INFO] events: Starting event system
^C
2026-02-10T12:03:49.008+0900 [INFO] service_registration.consul: shutting down consul backend
==> Vault shutdown triggered==> Vault server started!: 이 메시지가 떴다면 설정 파일(hcl) 로드에 성공하고 서버 프로세스가 점유되었다는 뜻입니다.
서비스 등록(모든 노드)
systemd 서비스 생성
sudo tee /etc/systemd/system/vault.service << 'EOF'
[Unit]
Description=Vault
Documentation=https://www.vaultproject.io/docs/
Requires=network-online.target
After=network-online.target consul.service
ConditionFileNotEmpty=/etc/vault.d/vault.hcl
[Service]
User=vault
Group=vault
ProtectSystem=full
ProtectHome=read-only
PrivateTmp=yes
PrivateDevices=yes
SecureBits=keep-caps
AmbientCapabilities=CAP_IPC_LOCK
CapabilityBoundingSet=CAP_SYSLOG CAP_IPC_LOCK
NoNewPrivileges=yes
ExecStart=/usr/local/bin/vault server -config=/etc/vault.d/vault.hcl
ExecReload=/bin/kill --signal HUP $MAINPID
KillMode=process
KillSignal=SIGINT
Restart=on-failure
RestartSec=5
TimeoutStopSec=30
LimitNOFILE=65536
LimitMEMLOCK=infinity
[Install]
WantedBy=multi-user.target
EOFVault 서비스 시작 및 활성화
sudo systemctl daemon-reload
sudo systemctl --now enable vault상태 확인
Vault 서비스 상태
sudo systemctl status vaultVault 초기화(node141에서만)
환경 변수 설정
export VAULT_ADDR='http://192.168.0.141:8200'Vault 초기화
vault operator init -key-shares=5 -key-threshold=3 | sudo tee /root/vault_info.txtUnseal Key 1: nw5hDaF+UcY1ZgeGLVpaeKZ2r9WO1kGYOldwqBWIfyuu
Unseal Key 2: /6vjAMgz7UdJwGVUZfz1iVLusvzMO2RrDOvg8pSdAO3z
Unseal Key 3: oR384IYlX92sf3K8kxEUjVwDwUGd0lKGIwCttRVkorpS
Unseal Key 4: b645WbRX4zLZ3enEg31YhaPIRCLX7gYd1IZ7ehHt1ONj
Unseal Key 5: Ly3zEVn5WfcZKZ8AOZmL6nKapiL2Sqc/zWoOM+XQ6aDS
Initial Root Token: hvs.2JkrW3kigeQX0YNlxNey5sda
...중요: 출력되는 Unseal Keys와 Initial Root Token을 안전하게 보관하세요!
Vault Unseal(모든 노드)
각 노드에서 3개의 unseal key를 사용하여 unsealing을 수행합니다.
node141
export VAULT_ADDR='http://192.168.0.141:8200'
vault operator unseal <KEY1>
vault operator unseal <KEY2>
vault operator unseal <KEY3>Key Value
--- -----
Seal Type shamir
Initialized true
Sealed false
Total Shares 5
Threshold 3
Version 1.21.3
Build Date 2026-02-03T14:56:30Z
Storage Type consul
Cluster Name vault-cluster-5a307b22
Cluster ID 79014df7-e6f5-22e5-6ff1-a605e1fa3314
HA Enabled true
HA Cluster n/a
HA Mode standby
Active Node Address <none>node142
export VAULT_ADDR='http://192.168.0.142:8200'
vault operator unseal <KEY1>
vault operator unseal <KEY2>
vault operator unseal <KEY3>Key Value
--- -----
Seal Type shamir
Initialized true
Sealed false
Total Shares 5
Threshold 3
Version 1.21.3
Build Date 2026-02-03T14:56:30Z
Storage Type consul
Cluster Name vault-cluster-5a307b22
Cluster ID 79014df7-e6f5-22e5-6ff1-a605e1fa3314
HA Enabled true
HA Cluster https://192.168.0.141:8201
HA Mode standby
Active Node Address http://192.168.0.141:8200node143
export VAULT_ADDR='http://192.168.0.143:8200'
vault operator unseal <KEY1>
vault operator unseal <KEY2>
vault operator unseal <KEY3>Key Value
--- -----
Seal Type shamir
Initialized true
Sealed false
Total Shares 5
Threshold 3
Version 1.21.3
Build Date 2026-02-03T14:56:30Z
Storage Type consul
Cluster Name vault-cluster-5a307b22
Cluster ID 79014df7-e6f5-22e5-6ff1-a605e1fa3314
HA Enabled true
HA Cluster https://192.168.0.141:8201
HA Mode standby
Active Node Address http://192.168.0.141:8200HA 상태 확인
환경 변수 설정
export VAULT_ADDR='http://192.168.0.141:8200'export VAULT_TOKEN='hvs.2JkrW3kigeQX0YNlxNey5sda'상태 확인
vault statusKey Value
--- -----
Seal Type shamir
Initialized true
Sealed false
Total Shares 5
Threshold 3
Version 1.21.3
Build Date 2026-02-03T14:56:30Z
Storage Type consul
Cluster Name vault-cluster-5a307b22
Cluster ID 79014df7-e6f5-22e5-6ff1-a605e1fa3314
HA Enabled true
HA Cluster https://192.168.0.141:8201
HA Mode active
Active Since 2026-02-10T12:35:47.868054113+09:00vault operator membersHost Name API Address Cluster Address Active Node Version Upgrade Version Redundancy Zone Last Echo
--------- ----------- --------------- ----------- ------- --------------- --------------- ---------
node141 http://192.168.0.141:8200 https://192.168.0.141:8201 true 1.21.3 n/a n/a n/a
node142 http://192.168.0.142:8200 https://192.168.0.142:8201 false 1.21.3 n/a n/a 2026-02-10T12:40:53+09:00
node143 http://192.168.0.143:8200 https://192.168.0.143:8201 false 1.21.3 n/a n/a 2026-02-10T12:40:52+09:00클러스터 리더 확인
consul catalog servicesconsul
vault방화벽 설정(선택)
# Consul 포트
sudo ufw allow 8300/tcp # Server RPC
sudo ufw allow 8301/tcp # Serf LAN
sudo ufw allow 8301/udp
sudo ufw allow 8302/tcp # Serf WAN
sudo ufw allow 8302/udp
sudo ufw allow 8500/tcp # HTTP API
sudo ufw allow 8600/tcp # DNS
sudo ufw allow 8600/udp
# Vault 포트
sudo ufw allow 8200/tcp # API
sudo ufw allow 8201/tcp # Cluster브라우저 접속 정보
Consul UI
http://192.168.0.141:8500/uiVault UI
http://192.168.0.141:8200/uiVault API
- 모든 노드의 8200 포트
HA 클러스터 구성이 완료되었습니다.
참고URL
- consul releases : consul_1.22.3_linux_arm64.zip
- vault releases : vault_1.21.3_linux_amd64.zip
'리눅스' 카테고리의 다른 글
| 우분투 24.04에서 TCP Wrappers를 사용하는 sshd 서비스를 접근 제어하는 방법 (0) | 2026.02.03 |
|---|---|
| Nginx 등록되지 않은 가상호스트를 차단 및 제한하는 방법 (0) | 2026.02.03 |
| CentOS 7에서 sg 드라이버가 로드되지 않았을 때 해결하는 방법 (0) | 2026.01.30 |
| CentOS 7에서 다운로드한 RPM 패키지 설치하는 방법 (0) | 2026.01.22 |
| HPE 서버 RAID 컨트롤러의 세대교체 (0) | 2026.01.19 |



