반응형
HashiCorp Vault를 Docker 컨테이너로 설정하는 방법
테스트 환경
$ docker version --format '{{.Server.Version}}'
28.2.2$ docker compose version
Docker Compose version v2.36.21. 디렉터리 구조 생성
mkdir -p ./vault/{config,file,logs}chmod -R 755 ./vault2. Vault 설정 파일 작성
vim vault/config/vault.json{
"storage": {
"file": {
"path": "/vault/file"
}
},
"listener": [{
"tcp": {
"address": "0.0.0.0:8200",
"tls_disable": true
}
}],
"ui": true
}3. docker-compose.yaml 파일 작성
vim docker-compose.yamlservices:
vault:
image: hashicorp/vault:latest
container_name: vault
restart: unless-stopped
cap_add:
- IPC_LOCK
entrypoint: ["vault", "server", "-config=/vault/config/vault.json"]
volumes:
- ./vault/config:/vault/config
- ./vault/file:/vault/file
- ./vault/logs:/vault/logs
ports:
- "8200:8200"
healthcheck:
test: ["CMD", "vault", "status", "-address=http://127.0.0.1:8200"]
interval: 30s
timeout: 10s
retries: 54. 컨테이너 실행
docker compose up -d컨테이너 상태 확인
docker compose ps로그 확인
docker compose logs -f vault728x90
5. Vault 초기화 및 언실
docker compose exec vault shexport VAULT_ADDR=http://127.0.0.1:8200초기화(init 시 생성되는 키와 root token은 꼭 백업)
vault operator init | tee init_backup.txt더보기
---
Unseal Key 1: aK0sqUsKov9pJ3a4wXEhnUC8CkKScA7XjlEy+0JdZyUB
Unseal Key 2: Jzk6qByqcFdqZYIMWcRS3rvUYRfI1TwXD3zmxIigyjen
Unseal Key 3: JUw5oLtA8qh6Myq5s5dCuzzBrol7Ohe7G1KRu3n/3Veg
Unseal Key 4: HnxytqkuqkBmF7KuMcKdvcSpBUtd9XiHB0qRy66wBqn8
Unseal Key 5: 9k1uxj5ErKrD5W4pAUuMERWhlb5jIfKHRNaWWyJ1iXjI
Initial Root Token: hvs.JIYu0JEuh1wUy6FEhQLwCrgs
Vault initialized with 5 key shares and a key threshold of 3. Please securely
distribute the key shares printed above. When the Vault is re-sealed,
restarted, or stopped, you must supply at least 3 of these keys to unseal it
before it can start servicing requests.
Vault does not store the generated root key. Without at least 3 keys to
reconstruct the root key, Vault will remain permanently sealed!
It is possible to generate new unseal keys, provided you have a quorum of
existing unseal keys shares. See "vault operator rekey" for more information.---
언실(init 시 출력된 Unseal Key 3개 이상 사용)
vault operator unseal <Unseal Key 1>
vault operator unseal <Unseal Key 2>
vault operator unseal <Unseal Key 3>상태 확인
vault statusKey Value
--- -----
Seal Type shamir
Initialized true
Sealed false
Total Shares 5
Threshold 3
Version 1.19.3
Build Date 2025-04-29T10:34:52Z
Storage Type file
Cluster Name vault-cluster-5183a175
Cluster ID fa285447-8e82-3c14-c4c6-9ac2ebc0d298
HA Enabled false6. 웹 UI 접속
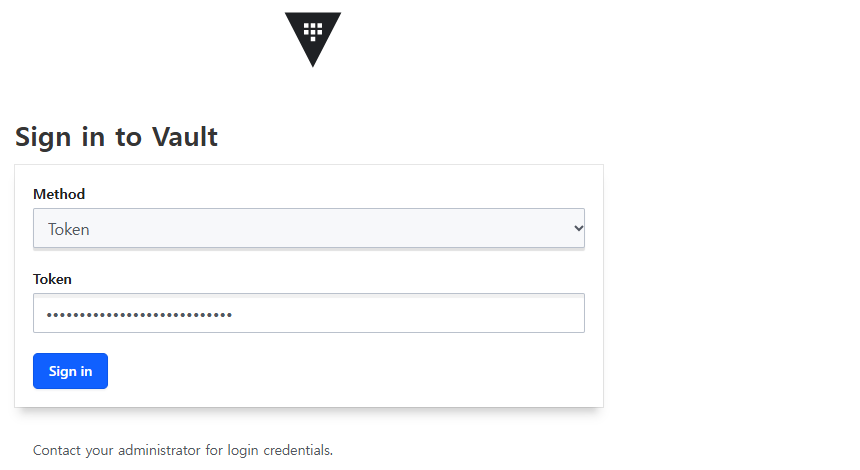
http://<호스트IP>:8200초기화 시 받은 Root Token으로 로그인하면 됩니다.
스크립트
# 디렉토리 생성
mkdir -p ./vault/{config,file,logs}
chmod -R 755 ./vault
# Vault 설정 파일 작성
cat <<EOF > vault/config/vault.json
{
"storage": {
"file": {
"path": "/vault/file"
}
},
"listener": [{
"tcp": {
"address": "0.0.0.0:8200",
"tls_disable": true
}
}],
"ui": true
}
EOF
# Docker Compose 파일 작성
cat <<EOF > docker-compose.yaml
services:
vault:
image: hashicorp/vault:latest
container_name: vault
restart: unless-stopped
cap_add:
- IPC_LOCK
environment:
VAULT_ADDR: http://127.0.0.1:8200
volumes:
- ./vault/config:/vault/config
- ./vault/file:/vault/file
- ./vault/logs:/vault/logs
entrypoint: ["vault", "server", "-config=/vault/config/vault.json"]
ports:
- "8200:8200"
healthcheck:
test: ["CMD", "vault", "status", "-address=http://127.0.0.1:8200"]
interval: 30s
timeout: 10s
retries: 5
EOF
# Vault 컨테이너 시작
docker compose up -d
# 로그 확인
docker compose logs -f vault
# Vault 초기화
docker compose exec vault sh -c 'export VAULT_ADDR=http://127.0.0.1:8200 && vault operator init'
# Vault 언실
docker compose exec vault sh -c 'vault operator unseal <Unseal Key 1>'
docker compose exec vault sh -c 'vault operator unseal <Unseal Key 2>'
docker compose exec vault sh -c 'vault operator unseal <Unseal Key 3>'
728x90
반응형
'리눅스' 카테고리의 다른 글
| HashiCorp Vault의 OTP 방식을 이용하여 SSH 인증을 구성하는 방법 (0) | 2025.06.16 |
|---|---|
| 우분투 24.04에서 Kubernetes를 제거 및 재설치 방법 (1) | 2025.06.16 |
| KEX 알고리즘 호환 문제 (0) | 2025.06.13 |
| 리눅스에서 SMB/CIFS 프로토콜을 이용하여 Windows 공유 폴더를 마운트하는 방법 (1) | 2025.06.11 |
| 우분투 22.04에서 Go를 설치하는 방법 (2) | 2025.06.11 |



